More IC vendors are beginning to explore a device-level technology approach for safeguarding data called physically unclonable function, or PUF. Though silicon production processes are precise, this technology exploits the fact that there are still tiny variations in each circuit produced. The PUF uses these tiny differences to generate a unique digital value that can be used as a secret keys. Secret keys are essential for digital security.
Security is increasingly becoming one of the big concerns for developers of connected, or internet of things (IoT), devices, especially with the huge risk they face from attacks by hackers, or compromises to information and security breaches.
One of the challenges for adding security in an IoT device is how to do so without adding silicon real estate or cost, given the resource constraints in terms of maintaing minimum power consumption and optimizing the processing resources on the devies.
With an effective implementation of PUF, it is possible to overcome the limits of conventional key storage: the PUF circuitry does not have a battery or other permanent power source. Attempts to physically probe the key will drastically change the characteristics of that PUF circuit and thus produce a different number. The PUF key can only be generated when it is needed for a cryptographic operation and can be instantly erased later.
The PUF technology provides advantages in terms of bill-of-materials (BOM) with the strong security of a tamper-proof SRAM. Although PUF technology alone is not enough to ensure key security, it certainly minimizes the vulnerability of embedded devices.
Recently, we saw product announcements from Maxim Integrated and Silicon Labs for secure devices using PUF technology. Silicon Labs added new hardware-based security for its wireless systems on chip (SoCs) for IoT devices in its Wireless Gecko Series 2 platform combining security software features with PUF hardware technology. Maxim Integrated introduced its MAX32520 ChipDNA Secure ARM Cortex-M4 Microcontroller, which similarly incorporates PUF for multiple levels of protection; its ChipDNA-generated key can be used directly for several functions such as symmetric secret to encrypt/decrypt data stored in the nonvolatile memory of the secure IC.
A spokseperson for Maxim told EE Times, “The MAX32520 can be used for any applications — even though we pointed out the IoT applications specifically in the announcement at embedded world, the IC is not limited to IoT applications.” The device addresses several applications, including industrial, healthcare, computing and IoT.

The MAX32520 can implement secure boot for any processor based on its serial flash emulation feature, and provides two additional physical layers: die shield and physical tamper detection. The chip offers internal flash encryption option. ?It is used for IP protection and flash data protection. The strong functions of crypto increase the trust of the device — it supports strong SHA512, ECDSA P521 and RSA 4096. The MAX32520 utilizes the ChipDNA output as key content to cryptographically secure all device stored data including user firmware. User firmware encryption provides ultimate software IP protection.
The ChipDNA can also generate a private key for the ECDSA signing operation. The MAX32520 provides a FIPS/NIST compliant TRNG, environmental and tamper detection circuitry to facilitate system-level security. Any attempt to probe or observe ChipDNA modifies the characteristics of the underlying circuit, preventing the discovery of the unique value used by the chip’s cryptographic functions. In the same way, more-exhaustive reverse-engineering attempts are canceled due to the factory conditioning necessary to make the ChipDNA circuit operational.

Meanwhile, Mike Dow, senior product manager for IoT Security at Silicon Labs explained to EE Times how they are utilizing PUF technology in its wireless SoCs for IoT devices. “For the physically unclonable function (PUF) embedded in Silicon Labs’ secure vault and secure element technologies, we use an SRAM PUF, meaning that it leverages the inherent randomness of a block of SRAM bits as they are powered up to derive a single symmetric key that’s unique to the device. We implemented SRAM PUF technology that has the longest proven track record of reliability in the market. Since the devices our customers deploy in the field often are operational for more than 10 years, we required PUF technology with a long history of reliability.”
He said in Silicon Labs’ implementation, it limits the use of the PUF to create a Key Encryption Key (KEK), which is used to wrap (encrypt) other keys in the system and store them in internal or external memory. “Because this KEK is only used to access wrapped keys, the amount of time it is in use is limited, which in turn limits its exposure to many types of attacks. In addition, the process of reconstructing the KEK only occurs on Power on Reset (POR) events, further limiting access to the process of generating the key.”
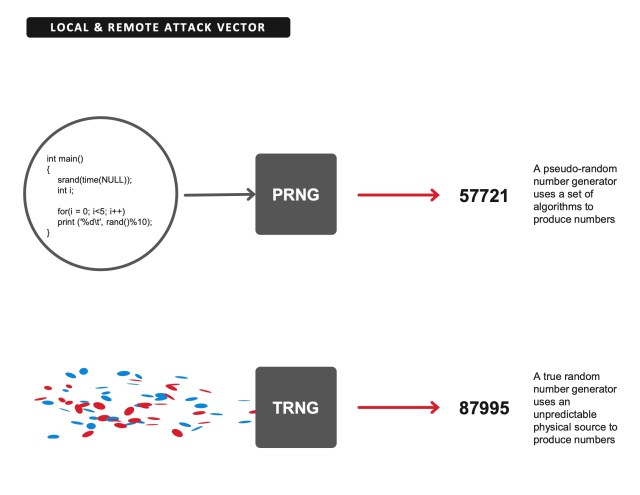
“In this design, every other key generation besides the KEK is performed by a NIST-compliant true random generator (TRNG), and then the key is wrapped with AES encryption. Both TRNG and AES technology is common, well understood, tested and verifiable in the security industry. We also use 256-bit keys for added strength of the AES encryption. We then apply differential power analysis (DPA) side-channel protection on the AES algorithm to strengthen it further against those attacks. All key material for the device is wrapped in this way including the ECC private/public identity key pairs generated and stored in one time programmable (OTP) memory.
The ability to store key material securely in almost unlimited internal or external memory is a major advantage when implementing complex cloud security schemes that require many multiple pairs of asymmetric keys. The alternative is to store the keys in plain text, but this approach requires very physically secure memories, which are both complex and expensive to protect.? Dow commented, “When designing the chip, you must choose an optimal size of secure memory. Yet, whatever size you choose, it is almost guaranteed to be insufficient over the life of the product.”

He said the other advantage of its secure vault key management scheme is that by using AES encryption, you can also require an initial vector to feed the algorithm. “This initial vector is like having an additional 128-bit password required to perform any security operation using that key. This password could then be used by either a human or another application running on our chip to provide a two-factor authentication to use the key.”
“As an added layer of protection, we have included a sophisticated tamper protection scheme in our secure vault technology that can destroy the PUF reconstruction data if a tamper is detected. Once the reconstruction data is destroyed, the stored key material can never again be accessed. This effectively “bricks” the device as no encryption algorithm can now be executed, preventing even a secure boot.”
Silicon Labs chose what it said is the most reliable PUF technology on the market and limited its function to providing only a single KEK to wrap or unwrap key material. That key can be further protected by requiring another two-factor authentication password. Dow added, “Additionally, we offer multiple tamper protection sources and can destroy the PUF key, making it useless for decrypting all other keys protected by it. Even if hackers invest considerable time and resources to reengineer the device and recover the KEK, they have compromised only a single device.”



























If the PUF logic is so sensitive, how can one be sure it's stable? It seems like a small environmental change could change it so that the KEK is different the next time it powers up, rendering it useless.